For over a decade, “Zero Trust” has been the buzzword in cybersecurity. You’ve probably heard the same refrain: “Never trust, always verify.” But strip away the vendor slides and the endless diagrams, and you find that Zero Trust isn’t really about technology; it’s about how and when trust is granted.
But are the traditional models not enough to gain trust? Why did Zero Trust become the most trusted security model? In this blog post, we will cover the limitations of the traditional model, how Zero Trust models help in securing the modern web, and how to implement a Zero Trust model.
Why Traditional Trust Models Fail?
The “trust but verify” model was designed for static networks. Today’s environments are borderless:
- Employees connect from coffee shops, airports, and remote locations.
- Applications run across AWS, Azure, GCP, containers, and SaaS platforms.
- Attackers use automated, persistent, and targeted methods.
Traditional models fail to maintain the security within modern infrastructure that is accessed by multiple ports, IP addresses, and networks. The Zero Trust model offers a modern alternative to traditional, perimeter-based security approaches that implicitly trust anything inside the network.
Common cloud-specific threats Zero Trust addresses:
| Credential Leakage | Attackers obtain API keys or secrets from public repositories, code, or mismanaged environments. |
| Privilege Escalation | Exploiting over-permissioned accounts or roles to gain access beyond intended limits. |
| Lateral Movement | Once inside, adversaries move between services (e.g., pivoting from a compromised container to sensitive data storage). |
| Shadow IT | Unmonitored assets and rogue cloud accounts exist outside of IT’s control. |
Let’s see what Zero Trust is, how it works, and how you can implement it.
What is the Zero Trust model?
The Zero Trust model is a modern cybersecurity approach built on the principle of “never trust, always verify.” Zero Trust treats every user, device, and application as potentially compromised, requiring continuous authentication, authorization, and validation of security posture before granting or maintaining access. By enforcing granular, context-aware controls and minimizing implicit trust, it significantly reduces the attack surface and strengthens resilience against both external threats and insider risks.
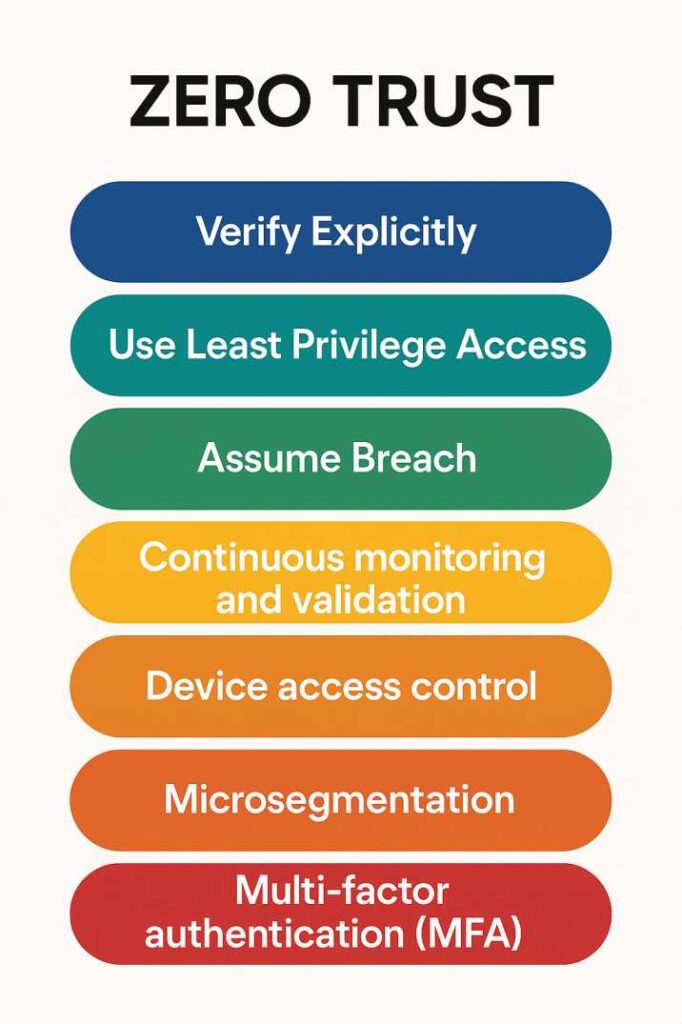
Core Principles of Zero Trust
Zero Trust is not a single process but a framework composed of multiple security practices that organizations must implement. To achieve a true Zero Trust security posture, businesses should apply its core principles across all systems, users, and data.
The core principles of the Zero Trust model are:
- Verify explicitly
- Use least privilege access
- Assume breach
- Continuous monitoring and validation
- Device access control
- Microsegmentations
- Multi-factor authentication
Let’s understand each one in detail.
1. Verify Explicitly
Always authenticate and authorize every access request using real-time context, such as user identity, device health, location, and data sensitivity. Don’t rely on implicit trust based on network location or device; require visible proof before granting access.
Example:
- Block access to a user logging in from a new country, even if their credentials are correct.
2. Use Least Privilege Access
Grant users and applications the minimum level of access required to perform their tasks, and nothing more. It limits the potential damage from compromised accounts or software vulnerabilities and helps contain breaches.
Best Practices:
- Implement Just-In-Time (JIT) access
- Enforce role-based access control (RBAC)
- Regularly audit and revoke stale permissions
3. Assume Breach
Design your environment with the expectation that adversaries might already have access. Limit lateral movement and blast radius by segmenting your network, monitoring aggressively, and planning for incident response in advance.
Real-World Impact:
- In the Capital One AWS breach, a lack of segmentation and misconfigured permissions allowed an attacker to exfiltrate 100M+ records. A Zero Trust approach could have blocked this lateral access.
4. Continuous Monitoring and Validation
Continuously evaluate user, device, and application behaviours. Use automated tools to verify access, monitor activity, and detect anomalies or policy violations as they occur. If you detect suspicious behaviour, you can quickly revoke or adjust access.
Tooling:
- AWS GuardDuty, Azure Sentinel, GCP SCC
- EDR/XDR tools like CrowdStrike and SentinelOne
- Anomaly detection via UEBA/SIEM
5. Device Access Control
Require all devices to be authenticated and regularly checked for compliance with security policies (such as up-to-date patches or endpoint protection) before granting them any level of access to cloud resources.
Tip: Integrate Mobile Device Management (MDM) or EDR solutions to enforce controls before allowing access.
6. Microsegmentation
Divide your cloud (and network) resources into tightly controlled segments or zones. Limit access between segments, enforce strict security policies, and use internal firewalls, security groups, or service meshes to block unauthorized movement.
Cloud Examples:
- AWS: VPC security groups + NACLs
- Azure: NSGs + Application Gateway
- Kubernetes: Istio or Linkerd service mesh
7. Multi-Factor Authentication (MFA)
Enforce MFA for all user and administrative logins, especially for privileged accounts. Use robust second factors (hardware tokens, authenticator apps), not just SMS. MFA stops many attacks that bypass passwords alone.
Advance Tactic:
- Use phishing-resistant MFA methods like FIDO2 or Passkeys instead of SMS codes.
How to adopt the Zero Trust Security Model?
Phase 1: Inventory & Identify (Foundation Building)
Objective: Gain complete visibility of what you need to protect.
Estimated timeline: 1-2 weeks
Key Actions:
- Inventory all users, devices, applications, APIs, and data stores across cloud, hybrid, and on-prem environments.
- Classify data by sensitivity (e.g., public, internal, confidential, restricted).
- Identify data flows — who accesses what, from where, and why.
- Map third-party access points and integrations (vendors, contractors, SaaS tools).
Recommended Tools:
- Asset Discovery: AWS Config, Azure Resource Graph, GCP Asset Inventory.
- Data Classification: Microsoft Purview, AWS Macie, open-source tools like Apache Atlas.
- Attack Surface Mapping: Shodan, Censys, or external ASM platforms.
Outcome: A complete, living asset map — the foundation for all trust decisions.
Phase 2: Enforce Strong Authentication (Identity First)
Objective: Ensure all identities are verified, secured, and context-aware.
Estimated timeline: 3-4 weeks
Key Actions:
- Implement MFA for all accounts — prioritize privileged/admin accounts first.
- Replace SMS-based MFA with phishing-resistant methods (FIDO2, Passkeys, YubiKeys).
- Enforce SSO (Single Sign-On) for all enterprise applications.
- Introduce conditional access policies based on device health, geolocation, and network type.
- Regularly rotate credentials, API keys, and service account secrets.
Recommended Tools:
- MFA & SSO: Okta, Azure AD, Auth0, Keycloak (open-source).
- Passwordless Authentication: Duo Passwordless, HYPR, Ping Identity.
- Identity Governance: SailPoint, Saviynt.
Outcome: Every access request is verified using strong, phishing-resistant authentication tied to context.
Phase 3: Least Privilege & Microsegmentation (Containment Layer)
Objective: Limit the damage possible if credentials or devices are compromised.
Estimated timeline: 3-4 weeks
Key Actions:
- Implement RBAC (Role-Based Access Control) and/or ABAC (Attribute-Based Access Control).
- Use Just-In-Time (JIT) access for privileged operations.
- Segment networks, workloads, and services to prevent lateral movement.
- Use service mesh (e.g., Istio, Linkerd) for workload-to-workload authentication.
- Enforce separation of duties for sensitive operations.
Recommended Tools:
- Access Management: AWS IAM Access Analyzer, GCP IAM Recommender.
- Microsegmentation: Illumio, Guardicore, Azure NSGs, AWS VPC Security Groups.
- Service Mesh: Istio, Linkerd, Consul.
Outcome: Even if an attacker breaches one component, they can’t easily move to others.
Phase 4: Behavioral & Contextual Security (Smart Trust)
Objective: Go beyond static access rules—make trust decisions adaptive to real-world conditions.
Key Actions:
- Deploy UEBA (User and Entity Behavior Analytics) to detect unusual activity.
- Establish baselines for normal user/device behavior (login times, locations, and access patterns).
- Trigger additional authentication or step-up verification when anomalies occur.
- Integrate real-time threat intelligence into access decisions.
Recommended Tools:
- UEBA & SIEM: Splunk UBA, Exabeam, Azure Sentinel, Chronicle.
- EDR/XDR: CrowdStrike Falcon, SentinelOne, Microsoft Defender XDR.
- Threat Intelligence Feeds: MISP (open-source), Recorded Future, ThreatConnect.
Outcome: Access adapts in real-time, reducing false positives while catching risky behaviour early.
Phase 5: Adaptive Trust & Automation (Self-Healing Security)
Objective: Make Zero Trust dynamic, self-updating, and measurable.
Key Actions:
- Assign real-time trust scores to all entities (users, devices, workloads).
- Automate policy updates based on trust score changes.
- Use SOAR (Security Orchestration, Automation, and Response) platforms for automated remediation.
- Continuously run breach simulations to test trust boundaries.
- Feed incident learnings back into the trust engine for continuous improvement.
Recommended Tools:
- SOAR: Palo Alto Cortex XSOAR, Splunk SOAR, Shuffle (open-source).
- Trust Scoring: Zscaler, Cisco Duo Risk-Based Authentication, custom ML models.
- Breach Simulation: AttackIQ, SafeBreach, Atomic Red Team.
Outcome: Security posture continuously improves without manual intervention; trust is never static.
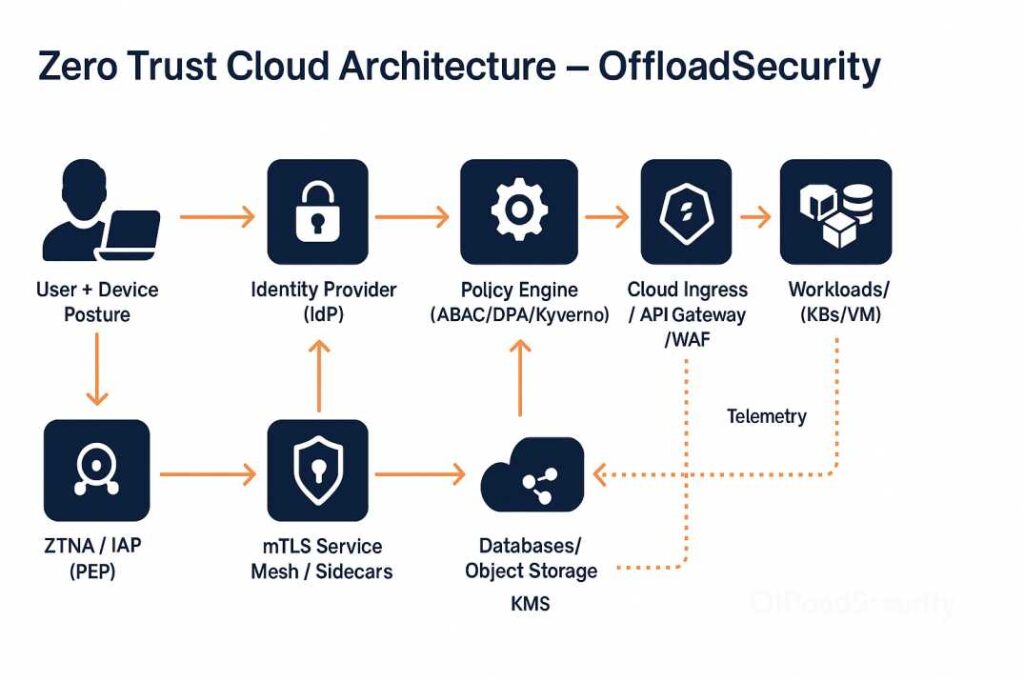
Cloud Zero Trust Architecture
The Zero Trust Cloud Architecture diagram illustrates how identity, device posture, policy engines, and secure access layers work together to enforce continuous verification and least privilege across cloud workloads and data.
Compliance Mapping
Implementing zero-trust control principles helps us comply with various compliance needs. For example, Verify Explicity satisfies the security practices covered in CIS Control 6.3, and HIPAA 164.312(d).
Similarly, in the following table, you can find the Zero Trust principle, and the corresponding compliance section it satisfies.
| Zero Trust Principle | NIST SP 800-207 | CIS Control | ISO 27001 | SOC 2 | PCI DSS | HIPAA |
| Verify Explicitly | 3.1, 3.4 | 6.3 | A.9.4 | CC6.1 | 8.3 | 164.312(d) |
| Least Privilege | 3.3 | 6.5 | A.9.1 | CC6.3 | 7.2 | 164.308(a)(4) |
| Assume Breach | 3.5 | 8.2 | A.16.1 | CC7.2 | 12.10 | 164.308(a)(6) |
| Continuous Monitoring | 3.6 | 8.7 | A.12.4 | CC7.3 | 10.6 | 164.312(b) |
| Device Access Control | 3.2 | 4.1 | A.9.2 | CC6.7 | 9.3 | 164.312(a)(1) |
Closing Thought
The original idea of Zero Trust was radical because it questioned the default assumptions of network security. But its real power is not in firewalls, MFA, or microsegmentation; it’s in designing systems that never take trust for granted. From this different perspective, Zero Trust is less about never trusting and more about continuously earning trust.
In this blog post, we covered what Zero Trust is and how to adopt it. But implementing Zero Trust in a real-world environment can be challenging. That’s where we come in. Our Zero Trust consulting service helps you navigate the complexities, avoid common pitfalls, and design a security strategy that works for your business from day one.
Get in touch for a free consultation and a no-obligation discussion about your Zero Trust implementation.