
Best Open Source Tools to Implement Zero Trust Security
Learn how to implement Zero Trust security step by step and explore the best open-source tools for identity, access, monitoring, and enforcement.

Learn how to implement Zero Trust security step by step and explore the best open-source tools for identity, access, monitoring, and enforcement.
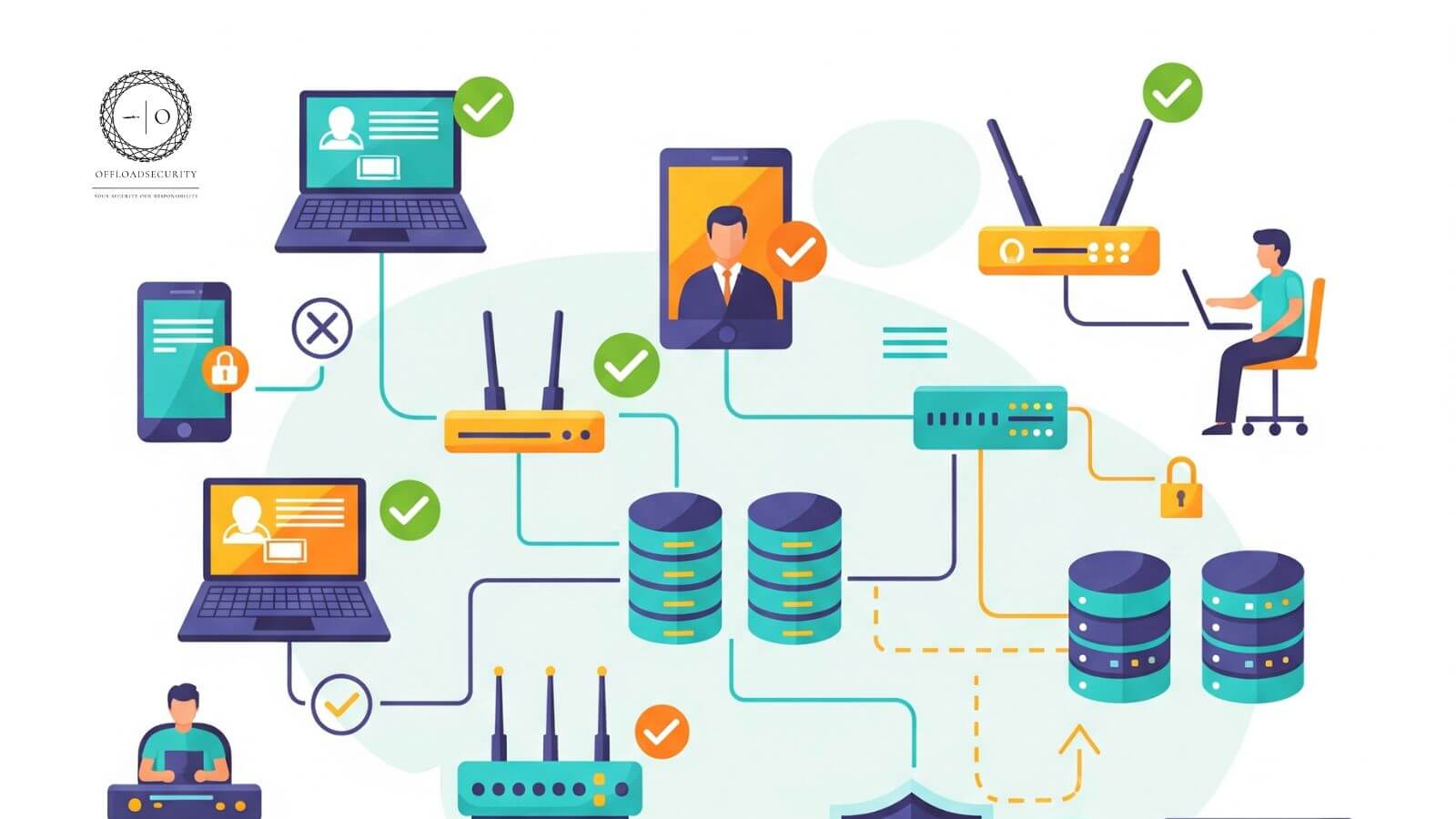
Learn what Zero Trust Security is, its core principles, why it is important, and how to implement it to protect systems from cyber threats.

Information is critical in modern world. Find out how you can protect information and what is information security?

Through the process of social engineering, threat actors manipulate people into giving the access to sensitive information. Below mentioned are the common methods used for Social Engineering.

NIST CSF framework offers direction derived from best practices and accepted standards. Learn more about it and how to use it.
Subscribe to our newsletter to receive security and compliance tips directly to email box.
No Spam, only value.
Offload Security is your trusted partner in cloud and enterprise security, ensuring compliance, resilience, and peace of mind through expert-driven solutions.
